The warning of publication of personal data follows the exploitation of a zero-day vulnerability, discovered this week, which impacted staff at organisations including airline British Airways (BA), broadcaster BBC, and pharmaceuticals provider Boots.
The vulnerability was found to be present within the MOVEit file transfer software, provided by US-based tech company Progress and utilised by HR software vendor Zellis — which handles the HR services of the companies affected.
Russian-speaking ransomware group Cl0p claimed responsibility for the attack, with researchers at Microsoft concluding that the threat actors were the culprits.
61,000 open source projects, vulnerable to 15-year-old flaw, now patched — An estimated 350,000 open source projects were found by Trellix to be at risk due to the CVE-2007-4559 vulnerability.
A date of 14th June has been stated as the deadline by Cl0p on its website, for organisations impacted to get in touch and pay a as-yet unspecified ransom in return for stolen payroll data, beyond which the group threatens to publish data over the Dark Web.
“This is announcement to educate companies who use Progress MOVEit product. If we do not hear from you until June 14 2023 we will post your name on this page… cal today before your company name is publish here,” said the message.
According to a Zellis spokesperson, both BA and Zellis have reported the attack to the Information Commissioner’s Office (ICO), with a BA spokesperson stating: “We have notified those colleagues whose personal information has been compromised to provide support and advice.”
A Boots spokesperson commented: “A global data vulnerability, which affected a third-party software used by one of our payroll providers, included some of our team members’ personal details.
“Our provider assured us that immediate steps were taken to disable the server, and as a priority we have made our team members aware.”
Dark web activity
Cybersecurity researchers Searchlight Cyber have already found signs of interest for data breached from the MOVEit exploit on the dark web, evidenced by the below screenshot:
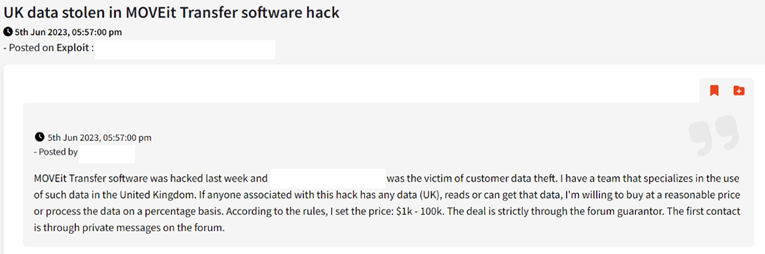
“Early this year we saw a zero day in the GoAnywhere software from Fortra cause havoc, with Cl0p alone ransoming over 100 organisations using the vulnerability,” said Ian Garratt, threat intelligence analyst at Searchlight Cyber.
“The MOVEit Transfer software — also reportedly being exploited by Cl0p — is a similar tool, allowing easy movement and sharing of files between locations. These types of Remote Code Execution are one of, if not the, most dangerous vulnerabilities because with the ability to run code of your choice on a target machine you can do literally anything.
“One of the ways hackers are using it is to steal corporate data and in this post on the dark web hacking forum Exploit — originally in Russian — a threat actor is requesting to buy data that has been stolen from one of the UK victims.
“This demonstrates how the criminal ecosystem works, with different threat actors specialising in different parts of the cyberattack. It also shows how quickly cyber criminals take advantage of a new exploit and the amount of money they expect to generate on stolen data.”
Security leaders concerned about dark web threats — A Searchlight Cyber study has revealed that the majority (93 per cent) of enterprise chief information security officers (CISOs) are concerned about dark web threats.
Who are Cl0p?
Believed to have undertaken criminal operations dating back to 2019, the Cl0p ransomware gang is derived from the Russian word “klop” which means “bedbug.”
While appearing to frequently utilise phishing email tactics, the gang has also been found to target numerous Common Vulnerabilities and Exposures (CVEs), including CVE-2023-34362 (the vulnerability present within the MOVEit software); CVE-2021-27101; CVE-2021-27102; and CVE-2021-27103.
Notable previous attacks carried out by Cl0p include:
- ExecuPharm (March 2020): Pharma corporation ExecuPharm were subject to a ransomware attack on social security numbers, financial information, driver’s licenses and passport numbers, among other sensitive information at the height of the pandemic. While claiming it would not target hospitals, nursing homes, or charities, Cl0p’s reported motive for the attack was that pharmaceutical companies “are the only ones who benefit from the current pandemic”.
- Software AG (October 2020): Also during the pandemic, upon breaching the infrastructure of enterprise software corporation Software AG, Cl0p became the first known ransomware group to demand payment above $20m, before publishing company data onto the Dark Web when an agreement couldn’t be made.
- South Staffordshire Water (August 2022): Cl0p claimed to steal 5TB of data — including scanned copies of passports and ID cards — from South Staffordshire Water employees. However the group misidentified the victims as Thames Water, with experts suggesting that this was a tactic to extort higher sums of money from a larger water supplier. South Staffs Water later insisted, however, that the attack didn’t compromise delivery of water supply.
Previous ransom demands made by the gang have ranged from $1m to $35m.
How to avoid getting hacked
To keep employee data protected, while maintaining operations, web application security provider Indusface advises businesses:
- Ensure incident response by reducing the attack surface, implementing preventive and detective controls, and regularly simulating attacks.
- Scan all applications used across the organisation for vulnerabilities.
- Deploy web application firewalls to keep further threats from infiltrating the organisation.
Garratt adds: “A patch is available for the MOVEit vulnerability and users should apply it as soon as possible, while closely monitoring or restricting network traffic to and from the software in the meantime to minimise risk of attack.”
Related:
The increasing impact of ransomware on operational technology — Dragos research has found a surge in ransomware attacks on operational technology, disproving that such threats only target IT.







