This article was updated 28/06/2017 17:19
The global cyber attack that affected firms across 64 countries yesterday may have started via corrupted updates on a piece of accountancy software. Experts are pointing to a Ukrainian tax-filing software, MEDoc, as the source of the infection, although the company denies it.
Ukraine bore the brunt of the attack, but Russia and other places in Europe were affected very rapidly. British advertising agency WPP was among a number of companies reporting problems.
Ukrainian firms were among the first to be hit, with the state power distributor and Kiev’s main airport affected. The Ukrainian central bank also reported problems. Ukraine’s deputy prime minister has tweeted a picture appearing to show government systems have been affected: “Ta-daaa! Network is down at the Cabinet of Minister’s secretariat.” Everything from banks and petrol stations was affected in this country.
>See also: The global ransomware attack a cyber wake-up call
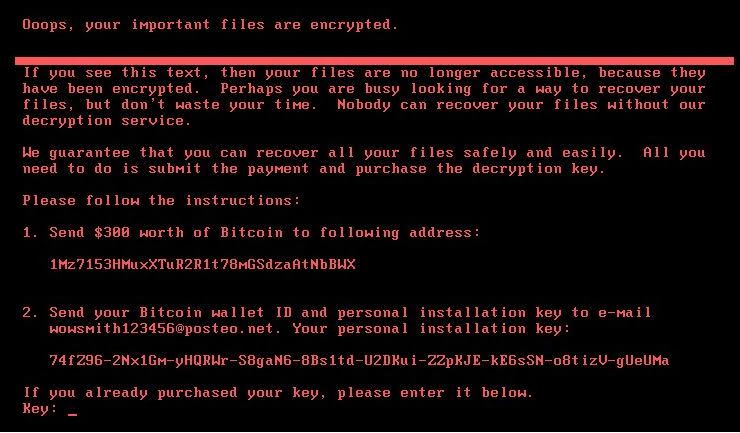
Initial reports suggested that the attack was a ransomware strain called Petya. However, in the aftermath initial investigations from some experts suggest the ransomware attack is a strain similar to Petya. GoldenEye is an improved version of Petya. Just like Petya, GoldenEye encrypts the entire hard disk drive and denies the user access to the computer. However, unlike Petya, there is no workaround to help victims retrieve the decryption keys from the computer.
There is some disagreement at the moment about what makes GoldenEye unique and whether it is a brand new malware sample. And, of course, there is some disagreement in terms of the initial infection vector, etc. We understand this.
Bitdefender, however, suggests that GoldenEye shares chunks of code with Petya, so it is clear that GoldenEye is an improved version of Petya. In other words, this new variant — GoldenEye — combines components from Petya, WannaCry and previous versions of GoldenEye, making it, in fact, a new threat.
Following on from other recent ransomware incidents, the outbreak is a reminder that preventative measures alone cannot provide full protection, and other failsafe measures – especially back-up – are a key aspect of business continuity assurance.
Andrew Stuart, MD, Datto EMEA commenting on this says: “As details emerge from this latest outbreak, we see again that preventative security measures are continuing to fail at stopping ransomware before it can cripple business networks. Although vulnerability scanning and anti-virus is an important measure in catching and blocking known strains, new ones – in this case rumoured to be related to ‘Petya’ – can pass through defences undetected before wreaking havoc.”
Global
Russian oil producer Rosneft and Danish shipping company Maersk continue to face disruption in its operations, including its offices in the UK and Ireland.
“We can confirm that Maersk IT systems are down across multiple sites and business units due to a cyber-attack,” the Copenhagen-headquartered firm said via Twitter.
“We continue to assess the situation. The safety of our employees, our operations and customers’ business is our top priority.”
>See also: UK firms sleepwalking into cyber attack chaos
Other countries in Europe were not spared either. Reports from the Spanish media suggest that multinationals like food giant Mondelez and legal firm DLA Piper were targeted in the attacks, while French construction materials company St Gobain has said it also a victim.
Ukraine’s deputy prime minister has tweeted a picture appearing to show government systems have been affected.
His caption reads: “Ta-daaa! Network is down at the Cabinet of Minister’s secretariat.”
As of yet few details are available, however, Patrick Hunter – director at One Identity has offered some early insight on the breaking news;
“Where are the lessons learnt? It seem that these types of attacks only happen to other people. Wrong! All computer systems are vulnerable, on all operating systems, on all versions. This again underlines the need for solid and easily to understand education for both users and management. Just because a company isn’t running Windows XP, it doesn’t mean that they are going to be immune. This latest tranche of ransomware seems to be hitting more modern versions.”
>See also: Flawless defence – how Glasswall protected itself from a cyber attack
“These aren’t attacks per se – they are not aimed or guided – they are just users clicking on things they shouldn’t and introducing the virus into their company network.”
“Securing the perimeter will help keep the wolf out but the users must stop inviting them in through the back door. This is how more insidious Trojans enter the network and can be used to syphon company data out of the network; user names, password s and credit card data. Controlling what the users have access to and limit them to what they need in order to do their jobs goes a long way to halt the spread of these sorts of viruses.”
It is not Petya!
The Petya comments were coming thick and fast, but Jeremiah Grossman, chief of security strategy at endpoint protection company SentinelOne had remained sceptial amid these reports.
“As with all cyber-attacks that spread as quickly as what we have seen today, there is always lots of speculation in the initial phase as researchers quickly come up to speed on the technical nuance of what the attack is and how it is spreading.”
“While many believe today’s outbreak is spreading via the EternalBlue exploit, we have not seen evidence of this as yet. This attack does appear to be using a similar method of collecting Bitcoin ransom that WannaCry had used, using only a small number of wallet addresses. Unlike WannaCry, we have yet to see if this outbreak has a kill switch, though we have found that the ransom won’t start until after a reboot. The malware is then allowed to spread for an hour before forcing the machine to reboot.”
“In addition, this outbreak has similar characteristics as Petya, such as infecting the MBR and encrypting the entire drive, however, it is not clear yet that this is a Petya variant.”
The UK’s largest conference for tech leadership, TechLeaders Summit, returns on 14 September with 40+ top execs signed up to speak about the challenges and opportunities surrounding the most disruptive innovations facing the enterprise today. Secure your place at this prestigious summit by registering here