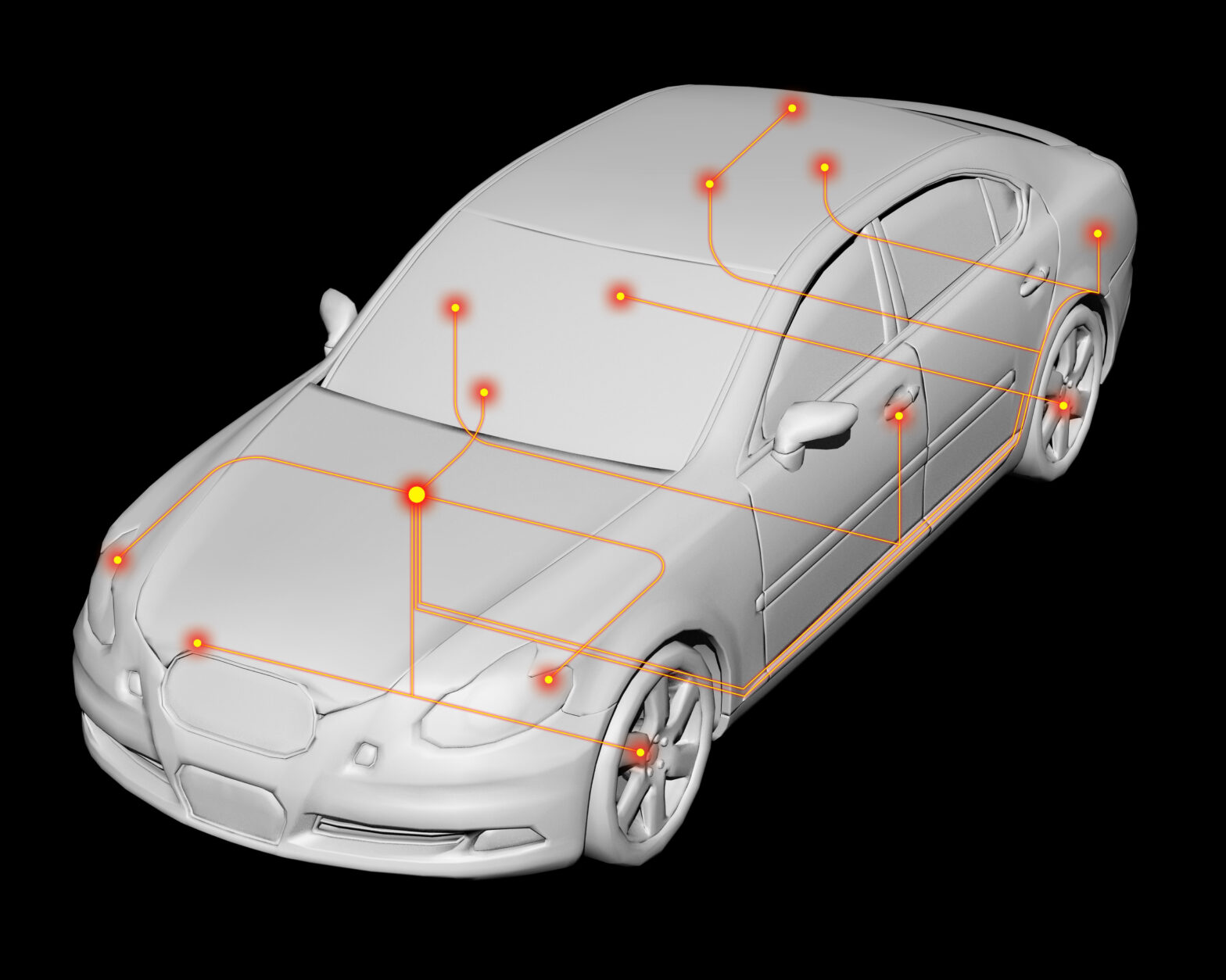
The prospect of the connected car offers many good reasons for drivers to be excited about the future. Not only will it contain a complete range of advanced safety standards throughout, it’ll undoubtedly change the driving experience beyond recognition.
At the same time as this anticipation, however, are concerns over aspects of the connected car’s security. And, with headlines around examples such as the disclosure that Nissan’s Leaf cars could be easily hacked, leading to the hijack of their air-conditioning and heating systems, these concerns might appear valid.
To further exacerbate these worries, recent research by global security consultancy IOActive revealed that, following tests, nearly every single component or device within a connected car was found to contain a flaw, at least half of which were vulnerable to potentially dangerous exploitation.
However, while attackers are unlikely to be terribly interested in your aircon, and it’s quite unlikely that they will be able to cook you with your heater, there is much work to be done as this current standard for connected components evolves, and more serious systems come on-line.
>See also: More connected cars equipped with data connectivity
So do news stories and the publication of research such as this mean that drivers are right to be worried? Even before they enter the mainstream, maybe there’s already a need to think about trading in the latest connected car for a more trustworthy and secure ‘analogue’ model.
Individual attacks unlikely
Before taking such a (perhaps) rash and reactionary move, however, it may be worth considering that being personally singled-out by a cyber attacker is a highly unlikely event.
Indeed, it’s most doubtful that one person would be perceived as sufficiently important, interesting or controversial that it warranted their car being directly hacked.
That said, security around connected cars should still be viewed as a serious issue – and certainly more serious than a cybercriminal hacking into an individual’s connected kettle or fridge.
Indeed, while a sophisticated attacker may not target a given individual, they may focus on one particularly vulnerable vehicle that could be used as an attack vector to the wider connected network.
Doing so would then allow them to cause chaos by targeting connected targeting transportation infrastructure or critical transport links.
To avoid such dire consequences, it’s important that businesses see this as a very possible threat, and one that absolutely shouldn’t be ignored.
Here then are three suggested steps that automotive manufacturers can take to protect connected cars from this potential threat.
1. Recognise that car is now more like a computer
With the combined computing power of more than 20 PCs, and containing over 100 million lines of code, cars today have more in common with an Apple iPhone than with a Mark II Ford Escort.
It’s important, therefore, that vehicle OEMs alter the way they address this changing concept. With today’s driving experience involving more software than ever before, every item of code involved must be securely encrypted and safeguarded against hackers.
2. Ensure rigorous authentication
Connected components require clear authentication processes to help defend them against cyber-attacks. It’s widely recognised by OEMs and suppliers alike that cryptographically-based digital signatures provide the strongest form of authentication.
It’s important, however, to remember that such processes require robust management and protection of the certificates and keys that underpin them, best achieved by working closely with those who have experience in protecting digital signatures.
>See also: Connected car production to grow rapidly in next 5 years
3. Safeguard vehicle-to-infrastructure communications by incorporating security-by-design technology
As vehicles begin to communicate more with infrastructure and other vehicles, it will become increasingly critical for managers to identify and implement those technologies necessary to protect a car’s drivers, passengers and the wider driving community from cybercriminals.
It’s clear that, with Gartner predicting a quarter of a billion connected vehicles on the road by 2020, there is a very real need to ensure that all of these vehicles are robustly safeguarded against cyber attacks.
While no particular individual may be under threat, those with malicious intent are likely to exploit vulnerabilities in the connected car as a means of accessing the wider transportation infrastructure or to use vehicles as tools in larger attacks. It’s up to car manufacturers to take the necessary steps now to make sure this gateway is well and truly blocked.
Sourced from Jon Geater, CTO, Thales e-Security