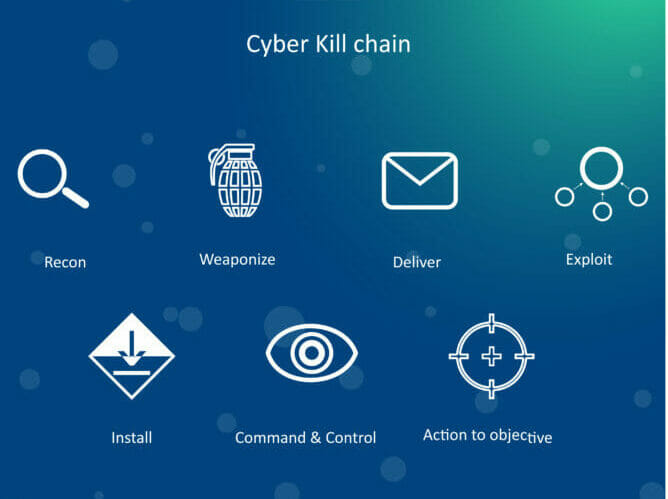
The term ‘kill chain’ was originally used as a military concept relating to structuring an attack into stages from identifying an adversary’s weaknesses to exploiting them. It consisted of target identification, forced dispatch to the target, decision, order to attack the target, and finally, destruction of the target. In simple terms it can be viewed as a stereotypical burglary, whereby the thief will perform reconnaissance on a building before trying to infiltrate and then go through several more steps before taking off with the valuables.
In 2011, Lockheed Martin put forward their own ‘Cyber Kill Chain’ to explain the various steps related to a digital attack. In the same way the traditional kill chain describes the seven steps in a physical attack, the cyber kill chain describes the modus operandi of a typical cyber attack:
- External Reconnaissance: Learning your victim’s weaknesses and choosing which attack methods will work with the highest degree of success.
- Weaponisation and Packaging: This takes many forms, such as web application exploitation, off-the-shelf or custom malware, compound document vulnerabilities delivered in PDF, Office or other document formats, or watering hole attacks.
- Delivery: The method and means of transporting or launching the attack can include many types of digital delivery mechanisms. The delivery of payloads is generally either target-initiated from visiting a malicious web presence or opening a malicious PDF file for example, or attacker-initiated, such as SQL injection or network service compromise.
- Exploitation: After delivery, the malicious payload will compromise the asset, thereby gaining a foothold in the environment. How this technically happens differs based on the type of digital attack chosen. In some cases, this involves a technical exploit mechanism, like specialised code that takes advantage of a vulnerability in software to ‘force’ something to happen on your computer. In other cases, the exploitation could just be a good phishing email, which socially engineers the victim to take some action themselves, like running malware or giving up credentials.
- Installation: The next step is to establish persistence on the victim system. This typically involves installing malware such as a trojan or bot client that will continue to run whenever the affected device reboots or turns on. This is usually designed to gain persistence at the endpoints where it has access and giving the adversary control of the application without alerting the organisation.
- Command and Control: This stage is simply setting up a communication mechanism, which security experts call the Command and Control (C2) channel to control the victim devices and exfiltrate data. This can be as simple as sending data over normal network services, like IRC, HTTP and others; or as complex as hiding specially encrypted traffic in tricky unexpected network services, such as hidden in DNS options or ICMP messages. Some modern threats even use social media mechanisms, like Twitter or Facebook posts, for command and control.
- Actions on Targets: This final phase covers the malicious actions which could be grabbing password hashes, installing ransomware, key logging, spying with your webcam, gathering any files and data you have, and much more.
Lockheed Martin’s original cyber kill chain didn’t properly cover a common stage of attack called lateral movement or pivoting. Often, the first device an attacker gains control of may not be the target so they must take additional steps to gain access to the real systems or data they need to accomplish their goal.
Lockheed Martin accounts for this by considering its cyber kill chain as circular, not linear. However, we believe that lateral movement and pivoting deserves a stage of its own, and we have proposed alternate versions of the cyber kill chain that remove the second stage, ‘weaponisation’, and replaced it with a new stage specifically for lateral movement and pivoting.
For those defending systems and data, understanding the cyber kill chain can help identify the differing and varying defences you need in place. While attackers are constantly evolving their methods, their approach always consists of these general stages. The closer to the start of the cyber kill chain an attack can be stopped the better, so a good understanding of adversaries and their tools and tactics will help to build more effective defences.
Five tech capabilities to shape your SME website security strategy
Endpoint defences can break the cyber kill chain
Cyber criminals look for the weakest point of entry to attack a corporate network. This is often through endpoint devices including laptops, tablets and phones, or other IoT and wireless devices. With the massive shift to working from home due to Covid-19, traditional corporate network security can’t protect users outside its perimeter. This means that your security strategy needs to strengthen defences on home workers’ endpoints.
Endpoint protection (EPP) can detect and prevent many stages of the cyber kill chain, completely preventing most threats or allowing you to remediate the most sophisticated ones in later stages. Endpoint protection should include multiple layers of malware detection, host firewalling and intrusion detection services, exploit detection and prevention capability, endpoint detection and response, web and email security capabilities, URL or IP/Domain filtering, patch management.
How to make cyber security intelligence-driven for a more proactive cyber defence
Let’s look at how these security layers help with some cyber kill chain stages:
- Delivery – Good EPP solutions apply many types of web or email malware detection, but looking only for known threats won’t protect against new variants or unknown attacks. So, it is important to combine traditional techniques such as signature-based analysis, heuristics and contextual detections with more proactive automatic detection techniques like behavioural analysis and classification using big data and machine learning, combined with a zero-trust model, which ensures any unclassified file or process will not run.
- Exploitation – Anti-exploit technologies can monitor endpoint memory for common exploit techniques that attackers use to trigger and leverage software flaws.
- Installation – As malware installs, or malicious stagers or droppers try to fetch additional malicious files, your layers of malware prevention can identify various indicators to prevent installation. EDR (Endpoint Detection and Response) functionality is designed to detect signs of malicious endpoint activity.
- Command and Control – Some EPP suites can monitor network traffic looking for indicators of ‘badness’. Whether part of the firewall, IDS, EDR, or URL, IP, or domain filtering, these EPP services can detect and often block Command and Control communications.
- Actions on Target – Good EDR solutions can identify when an endpoint does get infected and help remediate it by continuously monitoring activity such as identifying files being run, including their context of execution, which users ran which command or application and which data files were accessed. In short, it can identify malware running on an endpoint.
To mitigate and remediate a threat, EPP can block unknown application execution until it is validated by blocking any suspicious activity; quarantining malware; killing a compromised process – or even by completely shutting the system down.
The kill chain teaches us that while adversaries must completely progress through all phases for success, we just need to stop the chain at any step to break it. Attackers can often access the most valuable assets of an organisation via endpoints from home. Therefore, stopping adversaries at the endpoint drastically reduces the likelihood of success of any cyber attack.