The Dridex malware being distributed by TA575 was found by Proofpoint to be distributed via emails with subject lines relating to Squid Game, such as:
- Squid Game is back, watch new season before anyone else.
- Invite for Customer to access the new sesason. [sic]
- Squid game new season commercials casting preview
- Get early access Squid Game season 2.
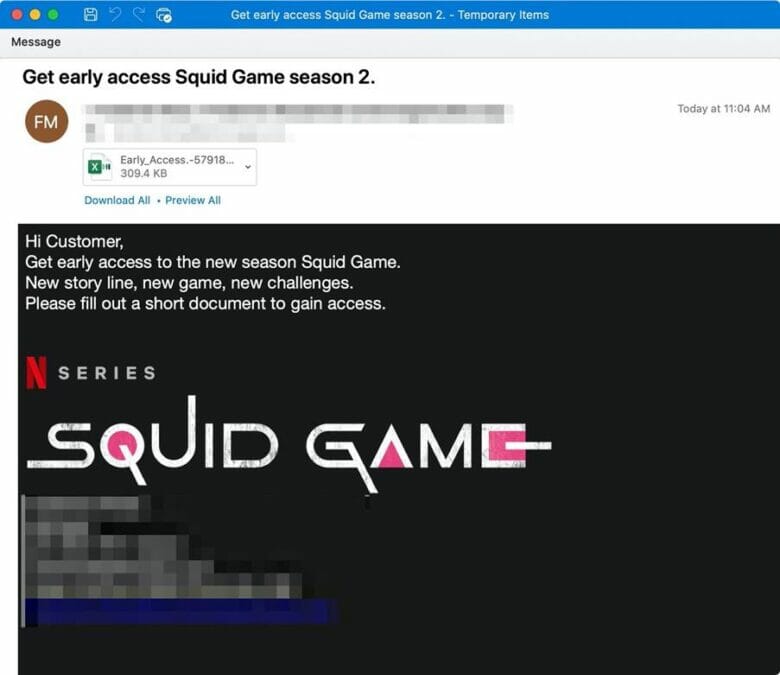
The emails tell targets, which were based all industries primarily in the United States, to fill out either an attached document to get early access to the new season of the show, or a talent form to become part of the background casting.
The attachments are Excel documents with macros that, if enabled, will download the Dridex banking trojan affiliate id “22203” from Discord URLs.
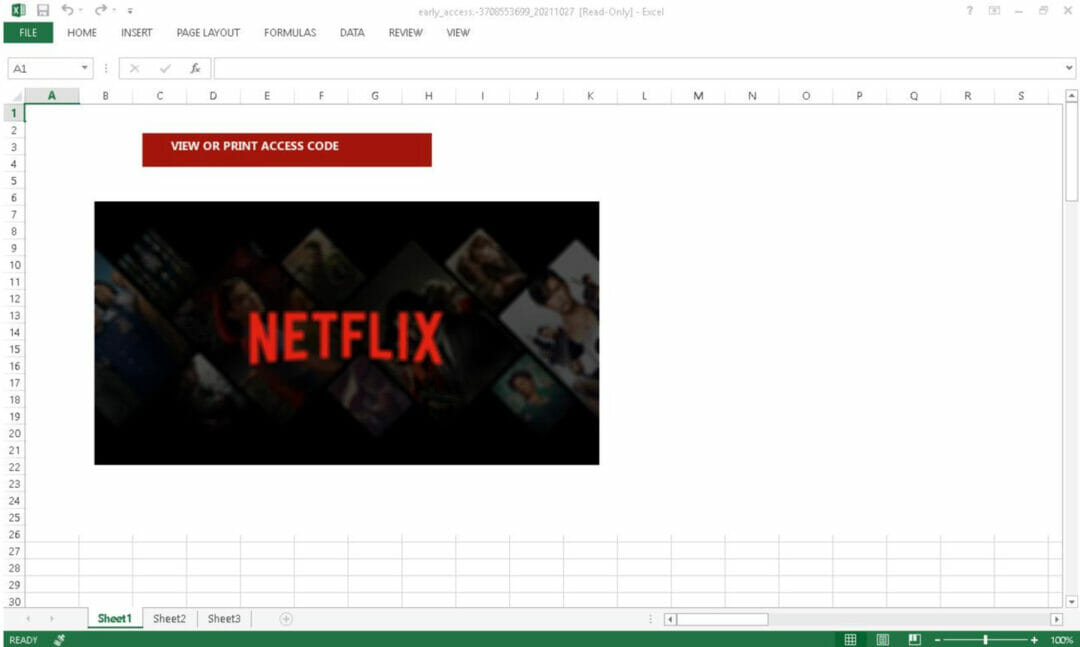
Dridex is a banking trojan distributed by multiple affiliates, including TA575, that can lead to data theft and installation of follow-on malware such as ransomware.
Cyber criminals are targeting the cloud — here’s how to defend against them
“TA575 is a Dridex affiliate tracked by Proofpoint since late 2020,” said Proofpoint analysts Axel F and Selena Larson, in the company’s blog post.
“This group distributes malware via malicious URLs, Microsoft Office attachments, and password-protected files. On average, TA575 sends thousands of emails per campaign impacting hundreds of organisations.
“TA575 also uses the Discord content delivery network (CDN) to host and distribute Dridex. Discord, a communications platform with consumer and enterprise uses, is an increasingly popular malware hosting service for cyber criminals.”







