The convergence of technology, especially in mobility, is driving the fourth industrial revolution.
“It’s here now,” stated Nick Dawson, global director, Enterprise Platforms Strategy and Business Development at Samsung, during his keynote at SOTI Sync 2019.
Accelerate your business and change expectations — SOTI Sync 2019
Before revealing these converging technology trends, he pointed to South Korea (and Asia in general) as an example to rest of the world.
“In Seoul and Asia in general [where Dawson lives and works], the rate of technology adoption puts the rest of the world to shame,” he said. Anyone who has lived in the region, Singapore or Shanghai for example, would agree with this statement. Driverless trains, automated garbage disposal (running under the city on conveyor belts), integrated fare systems and real-time information on how many seats are available on a specific bus are systems already in place in some of the countries in the region and “the rest of the world is in danger of falling behind and in some areas we are a decade behind,” warned Dawson. “In Asia, they adopt tech immediately; once innovated it’s put into action.”
The smart nation: Singapore’s masterplan
But, it’s not just one technology transforming business and society. It’s a convergence of technology trends, especially concerning mobility, that is driving the fourth industrial revolution in Asia and elsewhere.
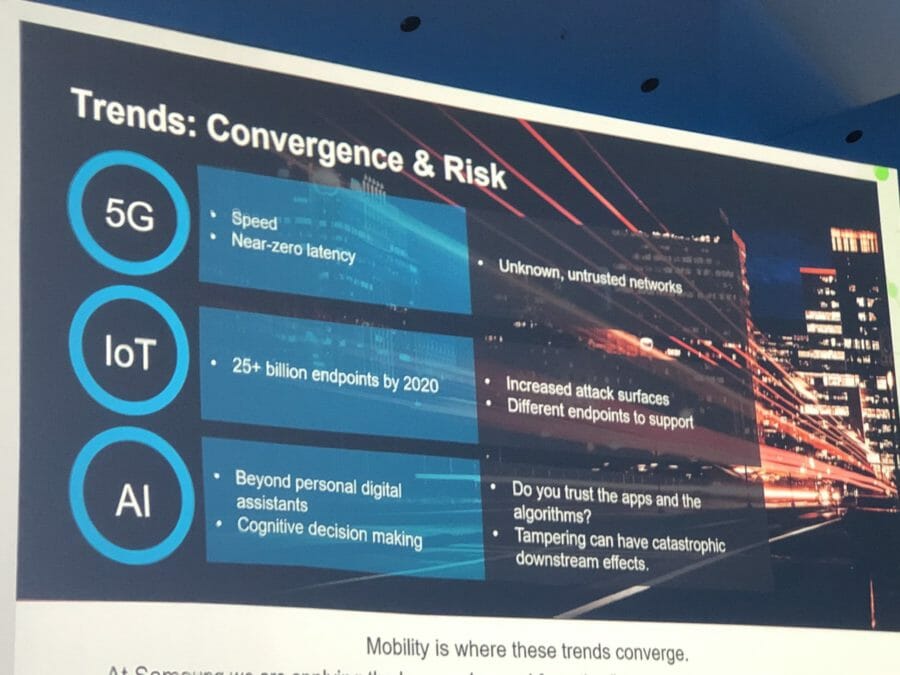
The convergence of technology
Dawson provided three technologies that are converging to drive transformation, but they all come with risks.
1. 5G: speed and near-zero latency
In today’s network infrastructure there are delays. These can’t be stopped and the length of delay can’t be predicted. With smart cities and autonomous vehicles on the horizon, this must be addressed, “because none of it can function with a delay,” explained Dawson. “5G is the catalyst of the fourth industrial revolution, because it opens up the ability to do what people have been talking about, and it will change the world.”
The risk: unknown and untrusted networks
2. IoT
“IoT has been waiting for 5G,” continued Dawson. “It will unlock IoT at scale.”
There are billions and billions of new connected endpoints and they will need to create and consume data at real world speeds on a constant and increasing basis — this won’t happen without 5G.
The risk: increased attack surfaces and different endpoints to support
3. AI
AI will be needed as a deicision support and automation tools to make sure of all this data. “We’re moving beyond personal digital assistants and into cognitive decision-making,” said Dawson.
The risk: do you trust the apps and tampering can have catastrophic downstream effects
There is no doubt that the convergence of these technologies will result in the transformation of how people do business and how they live. But, there is a problem. And, it’s the same problem that has cropped up time and time again:
Every network-connected endpoint must be inherently secure, but mobile security has never been a more urgent concern than it is today. What does this mean? At the dawn of the smartphone, the worry concerned security and manageability, and the same issues are relevant for internet connected devices: how can organisations secure and manage them?
CTO view: the growing convergence of information technology and operation technology
Securing the convergence of technology
First there’s a mindset shift that has to be adoptive. It’s less obvious or “intuitive” to secure sensors as opposed to smartphones, “but it’s just as important,” explained Dawson.
“Everything is connected whether they have a screen on or not. And the question [regardless of whether it’s a toaster or a smartphone] should be how do I secure the integrity of that device? Every device or appliance is a gateway or door the hacker can open.
Example: a casino was hacked through its aquarium’s environmental control system: the fish tank was the hackers door.
Risk mitigation in a hyper-mobile world
Dawson provided the audience with a comprehensive security strategy:
• Start with validated proven hardware, secure supply chain.
• Validated and secure firmware.
• Secure transport/networks.
• Security management infrastructure: unified endpoint management and mobile threat defence (AI is your friend).
• Buy into an open standards ecosystem (plug, play and swap as needed).
US Congress is introducing a new bill for IoT security; it’s time for the UK to follow
He concluded his keynote by explaining that most security solutions exist at top application layers. This is troublesome, because “a lower level of access has a higher access of privilege,” he said.
If these levels — the application layer, firmware/operating system and hardware — are not secured, then security is an illusion.
“You need security across all layers to ensure the integrity of a device.”







